IT-Sicherheits-Forscher Claudio Guarnieri hat eine Übersicht über die Malware der westlichen Geheimdienste erstellt: Everything we know of NSA and Five Eyes malware.
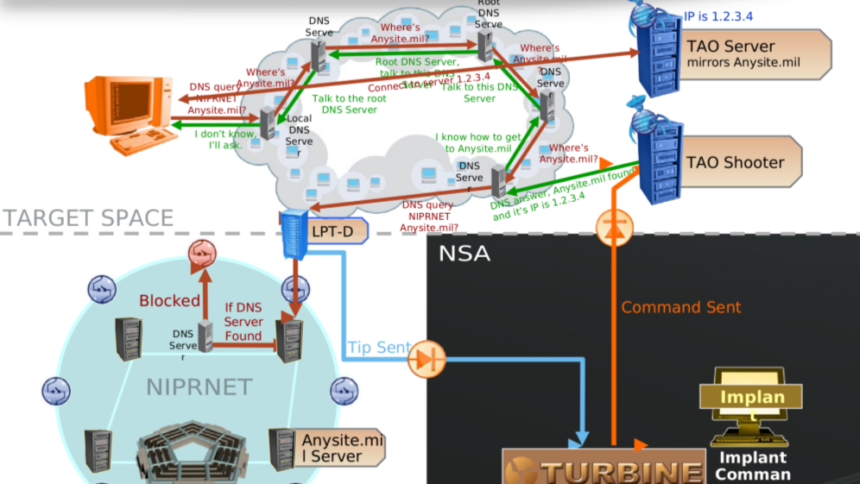
If there is one thing I can say for a fact, is that NSA has malware of all flavors. They have malware for all sorts of devices, platforms, architectures and networks. Their malware programs probably amount to dozens and NSA certainly has a different code name for each and every one of them. It is practically impossible to identify and understand all of them, but we can at least start with the ones that occur more often across the Snowden documents published so far.
It is very hard to have a clear understanding of the CNE and malware capabilities of NSA, GCHQ and Five Eyes as a whole. There is a large variety of programs and code names and it is clear that many of them are designed in such a way to be compatible and speak the same protocols. In some cases we can expect them to share parts of their code base as well.
The resources at their disposal are enormous, likely unmatched, and certainly their technical sophistication is equally remarkable. Assuming that Regin might in fact be WARRIORPRIDE, we can conclude that we still haven’t seen any of NSA’s malware programs in action. And if we did, we haven’t been able to identify which program they correspond to. My best bet is still on Flame.
Attribution is hard, and many criticize attempts of it as pretentious and most likely wrong. While I’m generally supportive of calling things for what they are, I’m learning that attribution of Western intelligence agencies attacks is incredibly hard. Regin is the closest we have got so far, and still, we likely won’t be able to differentiate one member of the Five Eyes from the others as a sole responsible for a given attack.
At this point much of what is known, and partly even what I explained here, is largely speculative. It is imperative that the technical community keeps conducting analysis of the information at our disposal, connect the dots and fill the blank spots left. Share what you have, publish what you know. Don’t hold back.



0 Ergänzungen
Dieser Artikel ist älter als ein Jahr, daher sind die Ergänzungen geschlossen.