Das CitizenLab berichtet über einen neuen Fund europäischer Staatstrojaner auf Rechnern von politischen Aktivisten autoritärer Regime: Hacking Team Reloaded? US-Based Ethiopian Journalists Again Targeted with Spyware
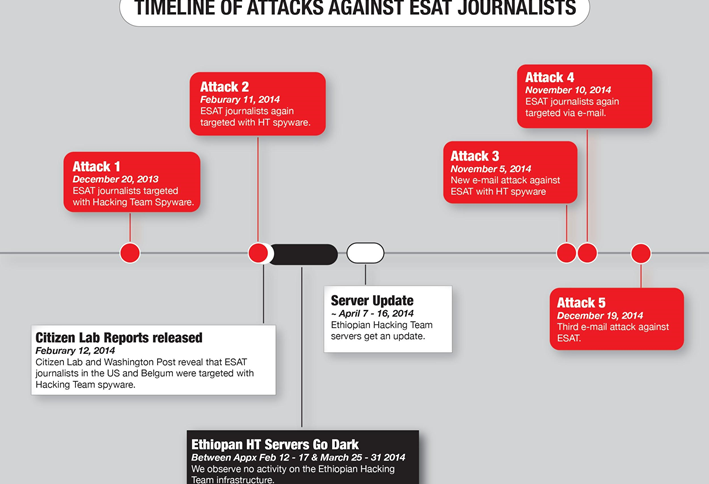
We have documented a year-long campaign of spyware attacks against journalists at ESAT, using what appears to be Hacking Team’s RCS spyware. Many of the journalists targeted in these attacks are legally considered US persons, and located in the US.
In its customer policy, Hacking Team notes:
[I]n HT contracts, we require customers to abide by applicable law. We reserve the right in our contracts to suspend support for our software if we find terms of our contracts are violated. If we suspend support for HT technology, the product soon becomes useless. We will refuse to provide or we will stop supporting our technologies to governments or government agencies … who refuse to agree to or comply with provisions in our contracts that describe intended use of HT software, or who refuse to sign contracts that include requirements that HT software be used lawfully.
The policy suggests that Hacking Team will cease support for its technology when a client violates terms of its contract by failing to abide by applicable law. The lawfulness of government targeting of individuals based in the US with spyware, however, is in question; for example, a lawsuit brought by a US citizen against the government of Ethiopia in February 2014 claims that such actions violated the US Wiretap Act.
Hacking Team has also publicly stated that they investigate abuses reported in the press and sometimes take action:
… we have investigated cases either discovered internally or reported in the press that suggest abuse. We can and have taken action in such cases, however, we consider the results of our investigations and the actions we take based on them to be confidential.
Our 2014 report documenting the abusive use of RCS against journalists received widespread media coverage, and both the Washington Post and Human Rights Watch corresponded with Hacking Team about our findings, and received specific responses.
In the wake of our 2014 reporting, we also sent an August 2014 open letter to Hacking Team, which inquired, inter alia, about investigation by the company into the reported misuse of the software against Ethiopian journalists in the United States. We posed further questions about their due diligence and accountability mechanisms, while applauding their efforts to incorporate human rights considerations into their customer policy. We have yet to receive a reply to this letter.
Despite the aforementioned public reports and correspondence, this report shows that the same attacker appeared to be receiving updated versions of the RCS spyware from Hacking Team as recently as November 2014.
Citizen Lab is sending an open letter to Hacking Team, providing a copy of this report and highlighting our reasons for concern from these latest findings. Hacking Team has recently announced that it is „complying fully“ with export controls adopted within the framework of the Wassenaar Arrangement, which includes language covering „intrusion software.“
Still, our findings suggest continued reasons for concern about the effectiveness of the mechanisms Hacking Team has in place to ensure respect for human rights in the use of their products.
Andrea Peterson berichtet für die Washington Post: Spyware vendor may have helped Ethiopia target journalists – even after it was aware of abuses, researchers say
The Ethiopian government appears again to be using Internet spying tools to attempt to eavesdrop on journalists based in suburban Washington, said security researchers who call such high-tech intrusions a serious threat to human rights and press freedoms worldwide.
The journalists, who work for Ethiopian Satellite Television in Alexandria, Va., provide one of the few independent news sources to their homeland through regular television and radio feeds — to the irritation of the government there, which has accused journalists of „terrorism“ and repeatedly jammed the signals of foreign broadcasters.
The struggle increasingly has stretched into cyberspace, where malicious software sold to governments for law enforcement purposes has been observed targeting the journalists, researchers said. The most recent documented case, from December, came several months after The Washington Post first detailed the government’s apparent deployment of the Internet spying tools, which though far cruder, offer some of the same snooping capabilities enjoyed by the National Security Agency and the intelligence services of other advanced nations.




0 Ergänzungen
Dieser Artikel ist älter als ein Jahr, daher sind die Ergänzungen geschlossen.