This is an english adaption of two German articles. Thanks to Anna and Kilian for their help on the translation.
Yesterday, we reported that the Twitter account @GammaGroupPR is publishing internal documents of the offensive computer intrusion product suite FinFisher/FinSpy, developed by Gamma and marketed and sold to state actors around the world. A post on reddit with the same username claims:
[…] a couple days ago when I hacked in and made off with 40GB of data from Gamma’s networks. I have hard proof they knew they were selling (and still are) to people using their software to attack Bahraini activists, along with a whole lot of other stuff in that 40GB.
Here’s a torrent of all the data. Please download and seed. Here’s a twitter feed where I’m posting some of the interesting stuff I find in there, starting off slow to build up rather than just publish all the worst shit at once.
If this Tweet is accurate, the hacked server is finsupport.finfisher.com, but it was since taken down.
Unfortunately, the Dropbox-accuont with the original Torrent-file is „temporarily disabled“, but we are happy to provide a mirror. (Magnet-Link)
The following are some of the files that were leaked on the Twitter account:
Portable Document Format (PDF):
- Cyber solutions for the fight against crime (17 pages)
- FinSpy 3.00 – User Manual – 2011-06-05, by Stephan Oelkers (127 pages)
- FinSpyPC 4.51 (HotFix for 4.50) Release Notes – 2014-04-14 (14 pages)
- FinSpyMobile 4.51 Release Notes – 2014-04-14 (15 pages)
Microsoft Excel:
- FinFisher Price list 2014 – 2013-12-16 (updated: 2014-01-24)
- FinFisher Products Extended Antivirus Test (Anti-Virus Results FinSpy PC 4.51) – 2014-04-04
- Device Tests FinSpyMobile 4.51 – 2006-09-16 (updated: 2014-04-15)
FinSploit Sales
There is a zip archive „FinSploit Sales“ with a text file and three videos.
The README contains those Frequently Asked Questions:
Q: Can you supply a list of the current exploits?
A: Yes but we need to do this individually for each request as the available exploits change on a regular basis.Q: Can we name the supplier?
A: Yes you can mention that we work with VUPEN hereQ: How does the customer get the exploits?
A: They will get access to a web-portal where they can then always download the available exploitsQ: Can this be used to deploy other trojans than FinSpy?
A: Yes, any exe file can be sentQ: Which Operating Systems do you cover?
A: Currently the focus is on Windows Vista/7. Some exploits for XP are also available. At the moment there are no 0 day exploits for OSX, Linux or mobile platforms.

The limitation to Windows 7 and Vista seems outdated. Two years ago, we reported that FinSpy Mobile also exists for all common mobile systems (iOS, Android, BlackBerry, Windows Mobile and Symbian). And last year, internal slides showed that FinSpy was able to infect all major operating systems (Windows, Linux and Mac OS X). If the newly published files are unmodified, they were created in October 2011, only a few days before ISS (Intelligent Support Systems) World in the US. Most likely this was the status for presenting it at this „Wiretappers Ball“, and since then the product range was expanded to all common systems.
Here are the three videos that show how vulnerabilities in three common software types are exploited:
- Windows 7 SP1 – Acrobat Reader PDF Exploit
- Windows 7 SP1 – Browsers Exploit
- Windows 7 SP1 – Microsoft Office 2010 DOC-XLS
Source code of FinFly Web
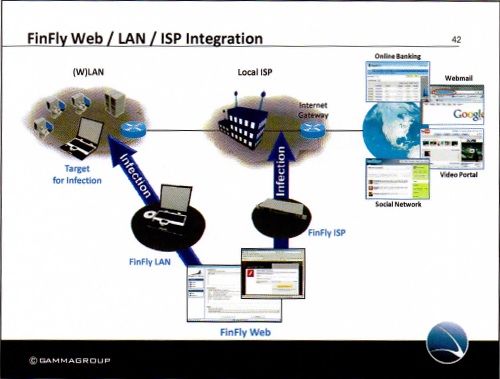 Another trophy is source code of FinFly Web, which found its way the code hosting platform GitHub. A company brochure that was published by WikiLeaks as part of the SpyFiles three years ago describes it like this:
Another trophy is source code of FinFly Web, which found its way the code hosting platform GitHub. A company brochure that was published by WikiLeaks as part of the SpyFiles three years ago describes it like this:
FinFly Web is designed to provide remote and covert infection of a Target System by using a wide range of web-based attacks.
FinFly Web provides a point-and-click interface, enabling the Agent to easily create a custom infection code according to selected modules.
Target Systems visiting a prepared website with the implemented infection code will be covertly infected with the configured software.
A video advertises its features, and other documents describe provide more details.
Malware researcher: „This guy is a malware developer“
Raphaël Vinot, a malware researcher from France, has since decompiled a few java class files to make the code more understandable. He told netzpolitik.org (as himself, not his employer):
Yesterday, I just had a very fast look at the repository and decompiled a few class files. The website is a testing instance to show to the new clients what they can do.
I don’t think there is anything particularly interesting in that code, but it is a very good platform to show to non-technical people what attackers can do and how it will look like in the wild.
I am personally going to reuse it at cyptoparties.
The most interesting thing I found is in the file SearchEnhancer.java, which references the website www.codito.de. This redirects to www.mushun.de, which in turn lists Martin J. Muench in the imprint. MJM used to work for Gamma GmbH and acted as a speaker for the company.
This guy is a malware developer and has to be treated like one. I really hope the clients are going to be revealed soon-ish, but most especially detections and indicators so it will be possible to share them with companies and other partners in order to detect FinFisher in the wild.
FinFisher: „We don’t want to comment on this“
Today we called them again, and again the answer was: „We don’t want to comment on this.“ This time around, they greeted us with „FinFisher here“ instead of denying it at first. When we asked, if we could speak to Martin Muench, we were rejected again:
netzpolitik.org: Is Mr. Muench available? I already talked to him before.
FinFisher GmbH: You already talked to him before?
netzpolitik.org: Yes, but that was a while ago. Maybe last year.
FinFisher GmbH: Mr Muench is not in the house.
netzpolitik.org: Not at all or just at the moment?
FinFisher GmbH: […]
netzpolitik.org: ?
FinFisher GmbH: Definitely not now.
We have heard rumors that Martin ‚MJM‘ Muench does not work for Gamma/FinFisher anymore. If you have more information on this (or anything else on the topic): don’t hesitate to contact us!
Human rights activist: „such techniques are not lawful“
Eric King, Deputy Director of the UK-based charity that defends and promotes the right to privacy across the world, told netzpolitik.org:
In the last few years, a spotlight has been shone on the secretive practice of government hacking. This completely unchecked area of intelligence collection amounts to some of the most intrusive forms of surveillance any government can conduct.
FinFisher are one of the most aggressive companies to try and supply the worlds law enforcement agencies with such tools, but without public debate, and clear laws authorising their use – such techniques are not lawful. Privacy International and EFF have both filed lawsuits on behalf of activists who have been targeted by the Ethiopian government using FinFisher. Many more activists will have been targeted by repressive regimes, and surveillance companies like FinFisher must take responsibility for their role in that repression, and stop their damaging practices.
Security researcher: „generally considered criminal behavior“
Yesterday, Jacob Appelbaum, computer security researcher and hacker, told netzpolitik.org:
This document release shows that those responsible for protecting our security are aware of bypasses for commonly advocated security technologies. As an example, anti-virus bypass, which is a well known issue – is compounded by the desire for certain attackers to ensure that bypassses are not fixed but rather exploited. There is a dual role here and the overall security of our computers is being subverted by this dual role – to protect and the desire to infect protection loses in service of attacking people. Furthermore, we see that these government customers are aware that FinFisher is defrauding companies and their users by abusing their branding, logos and names – something that is generally considered criminal behavior when done by any other actor on the internet.
These exploitable issues in commonly used software – in our everyday telephones, personal computers and in our infrastructure – are problems that need to be fixed; rather than fixing them, they are being exploited and are left vulnerable for any attacker, regardless of motive.
Today, Jacob Appelbaum adds:
This larger release of 40GB of data raises many interesting questions – impersonating companies such as RealPlayer, Adobe, and others has been well documented by third parties; we now have further evidence of such attack vectors as well as the government officials who were party to this kind of fraud for their own benefit.
We hope, that there are many more interesting things to be found in the 40 GB torrent download. Please post your findings in the comments.



20 Ergänzungen
Dieser Artikel ist älter als ein Jahr, daher sind die Ergänzungen geschlossen.